
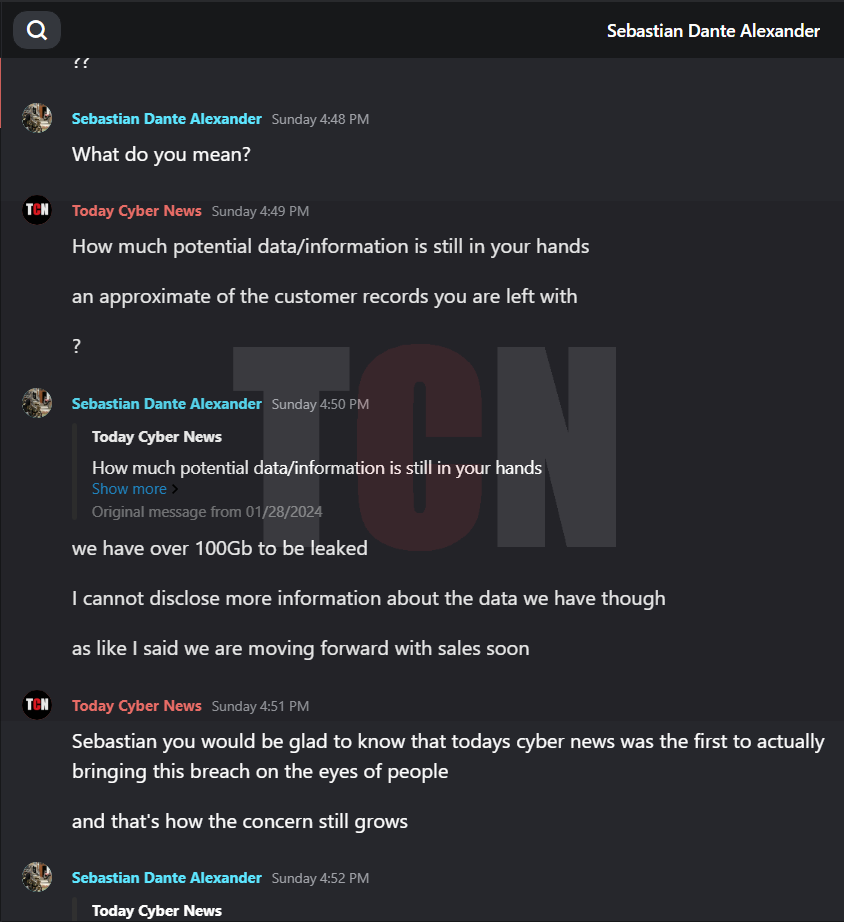
Big trouble in Jakarta! The mighty railway company, Kereta Api Indonesia (KAI), has been attacked by a notorious hacking group called STROMOUS.We attempted to reach out to various members of the hacking group and managed to arrange an interview with the leader of ghostsec Hacker group successfully. Stormous carried out the breach around a week before @TodayCyberNews revealed the leaked information on their X account last Sunday.
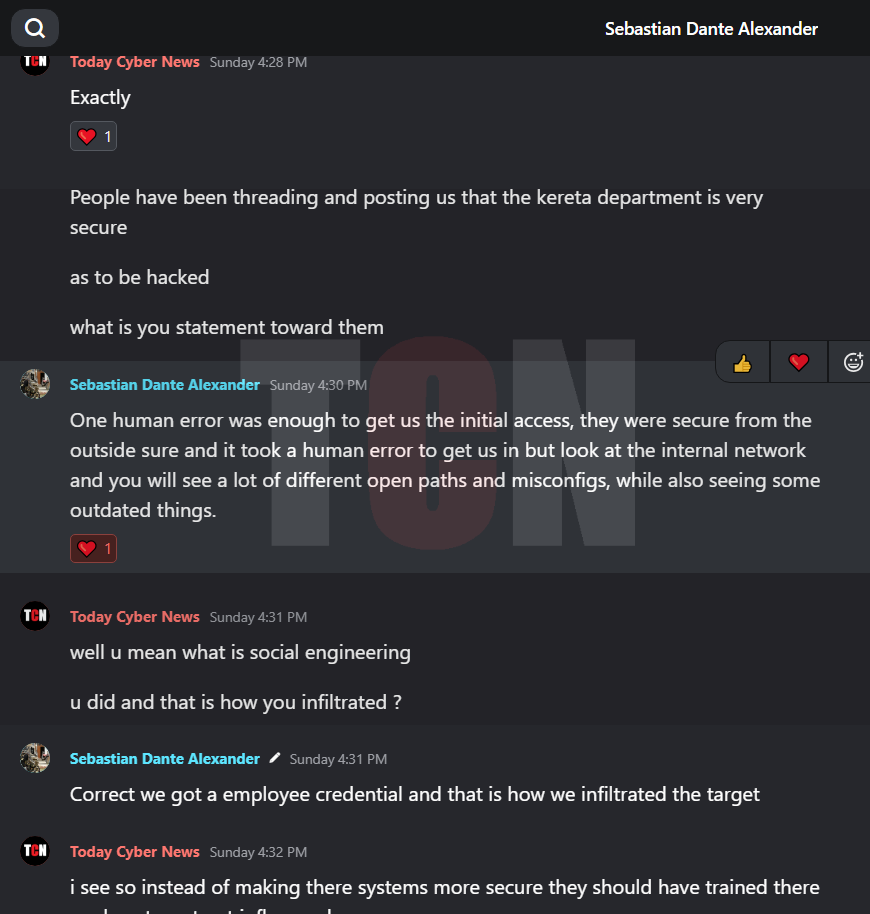
During our exclusive interview with the leader of ghostsec hacker group, a wealth of information about the hacking incident was unveiled. Our discussion delved into extensive insights, ranging from understanding the hacking group’s background to unravelling the social engineering tactics used to infiltrate Kereta’s staff and breach the system, ultimately leading to the imposition of a ransom for data leakage.
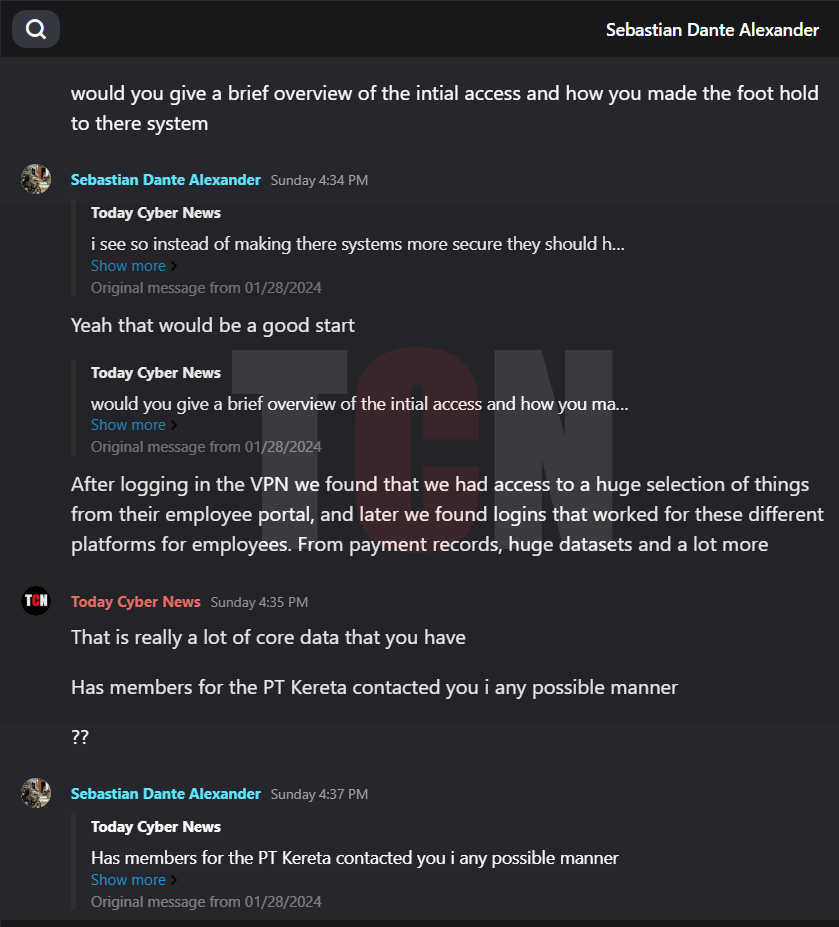
Stormous successfully gained access to KAI’s dashboards, possibly through a variety of methods like social engineering, phishing, or purchasing credentials from other hackers. They shared screenshots to prove their entry, demonstrating that they did so through internal employee channels.

In a brief summary of the interview, the leader of the hacking group GhostSec, revealed that they are a group focused on hacking as an art form and enjoy every aspect of it.
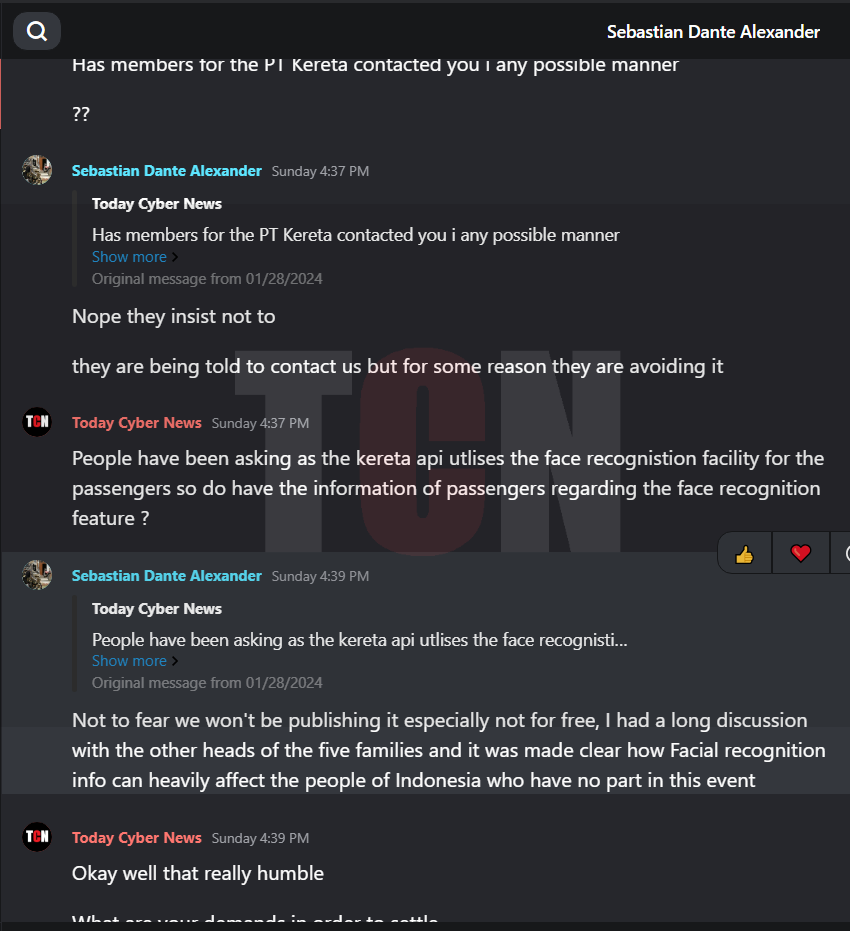
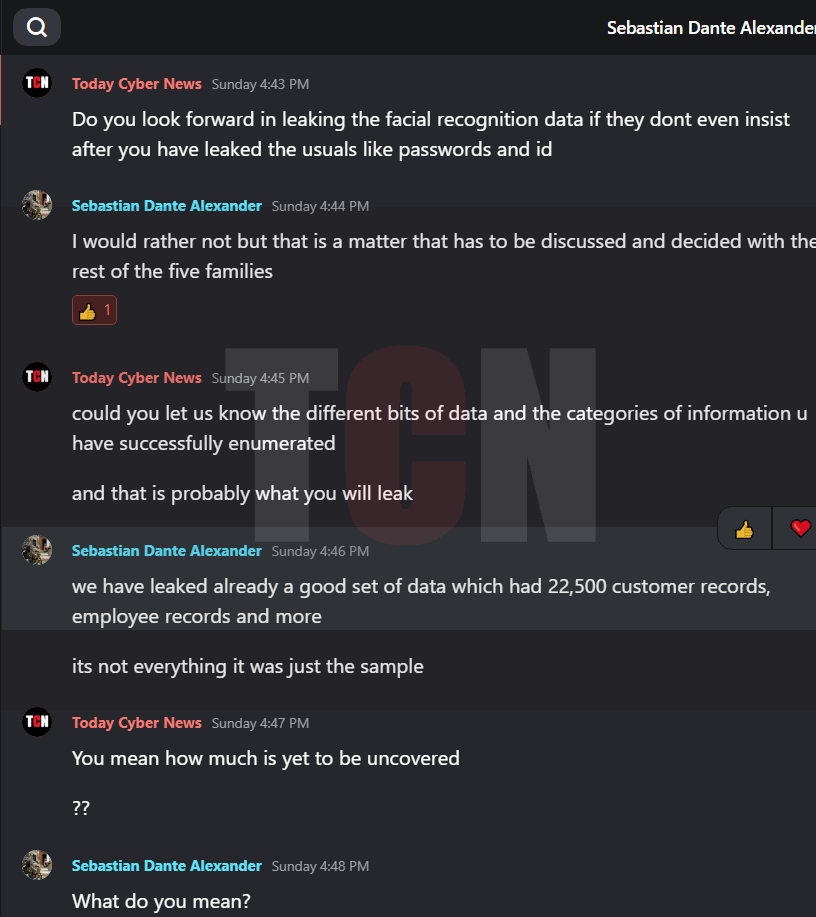
In the interview, the person was asked about their involvement with Kereta Api and how they managed to gain access to systems. They responded by stating that, while financial gain was a factor for other groups, their main motive was to demonstrate that hacking train stations is possible. They also expressed concerns about privacy invasions and the use of AI facial recognition technology. They admitted to infiltrating the target by obtaining an employee credential.We are pleased to present the interview excerpt, corroborated with relevant screenshots.
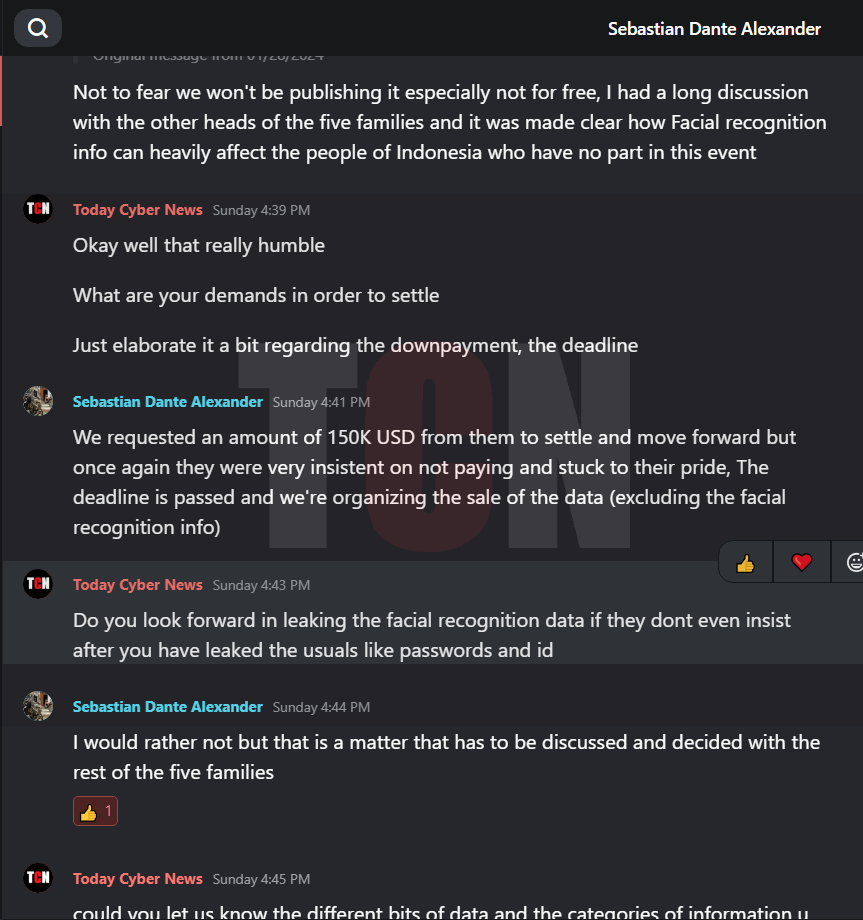
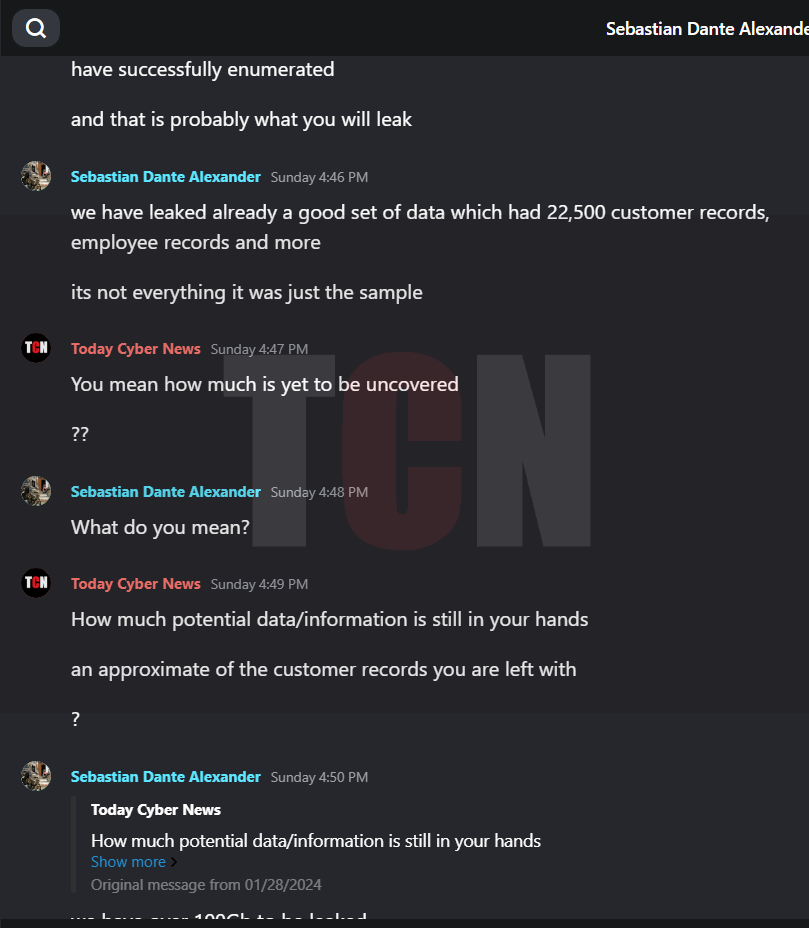
The Hacker explained that they had asked for a ransom of 150K USD from the concerned party as a means to settle the issue and move forward. However, the other party remained adamant and refused to pay, primarily due to their pride. The deadline for payment has since passed, and as a result, they are now making arrangements to sell the data, excluding the facial recognition information.
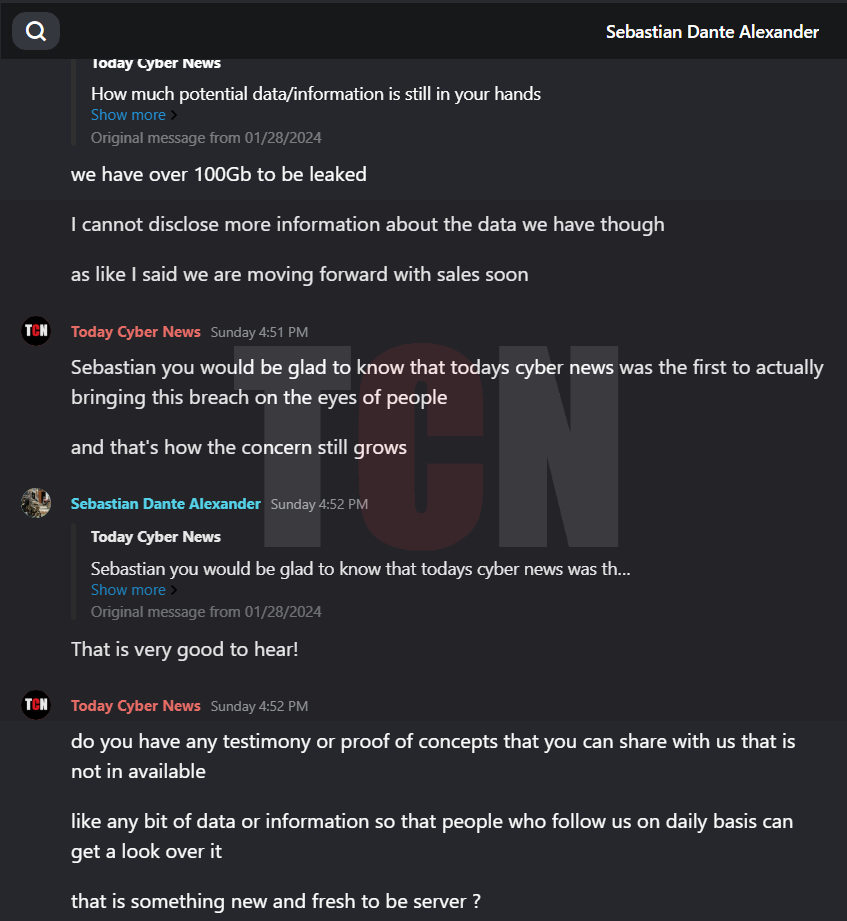
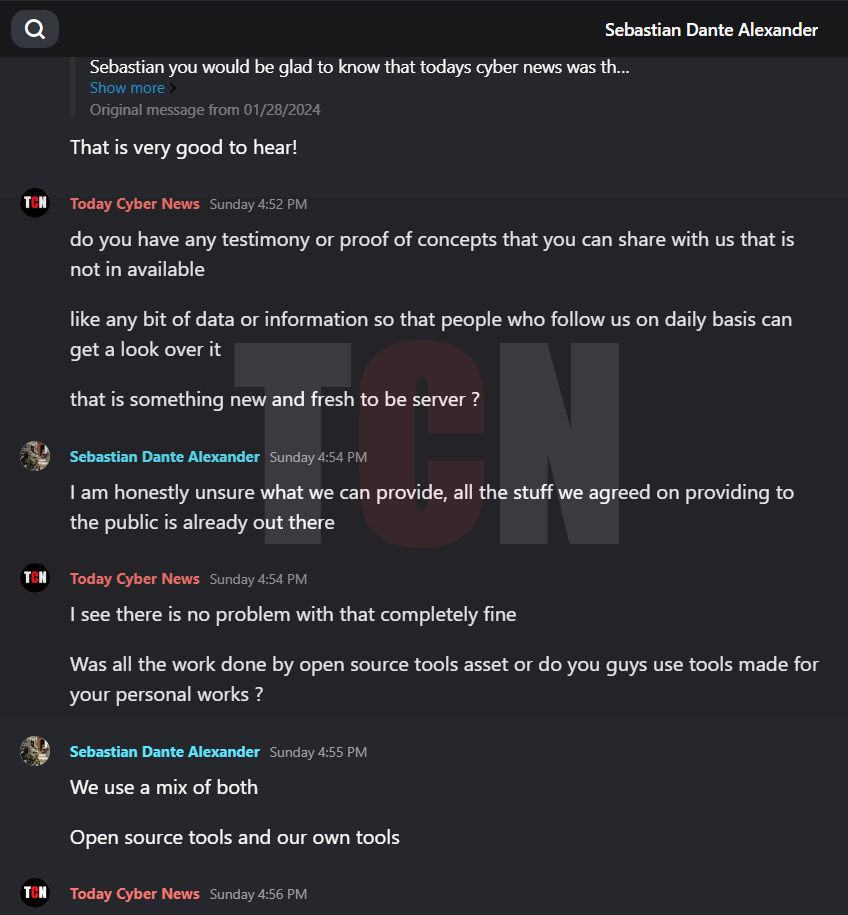
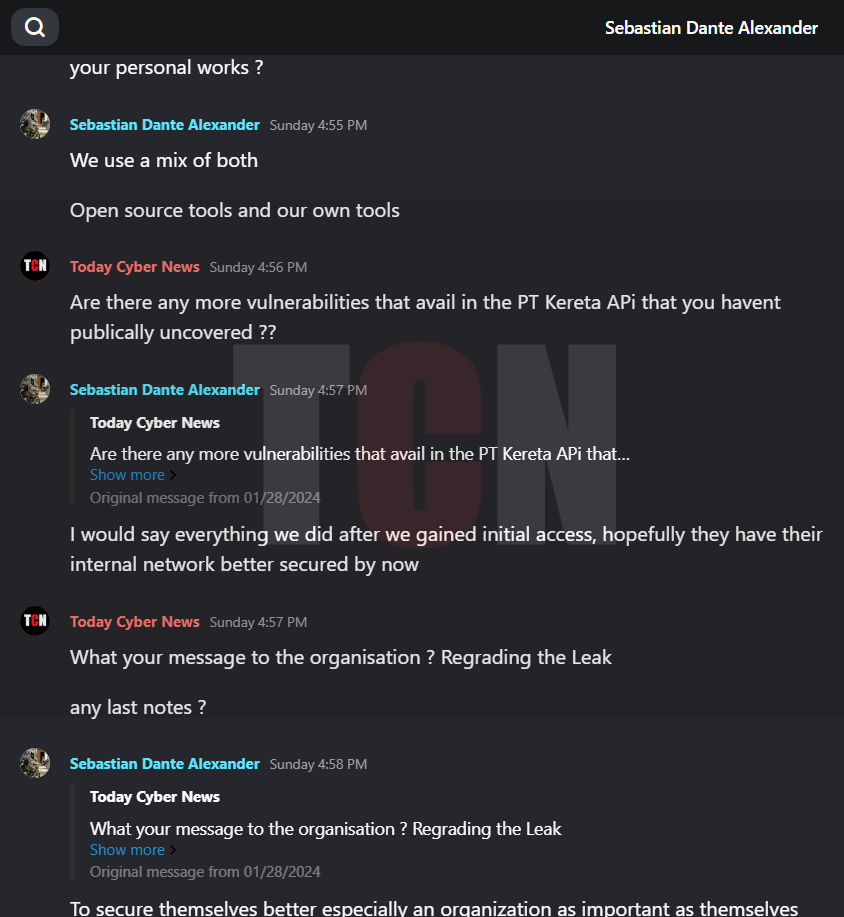
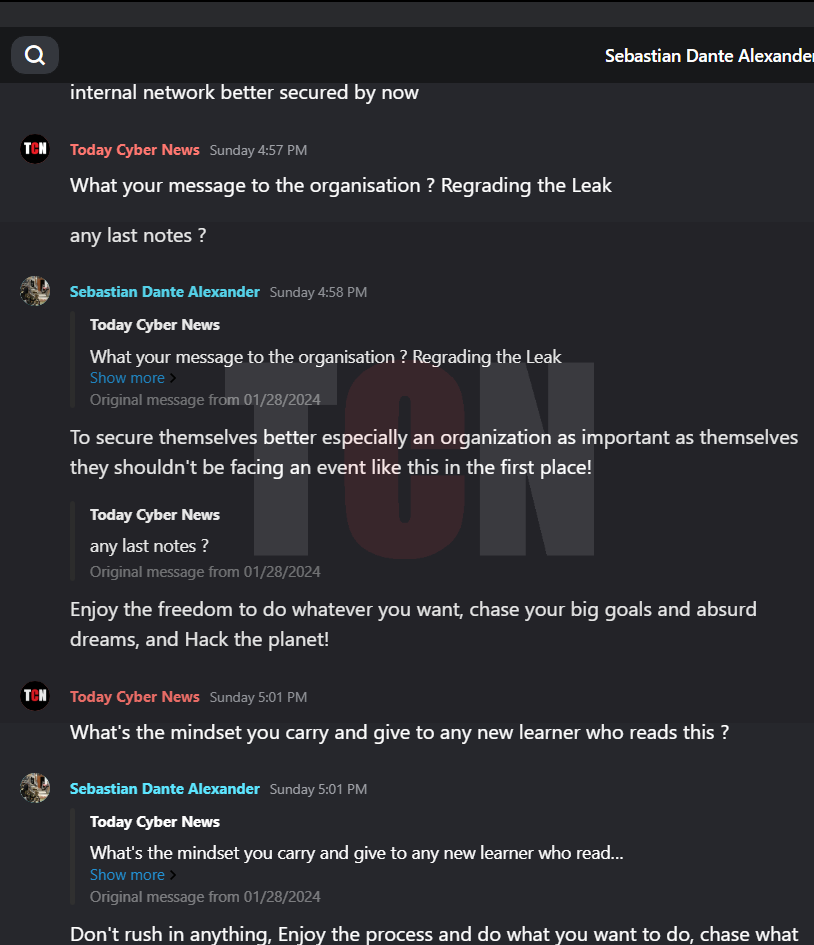
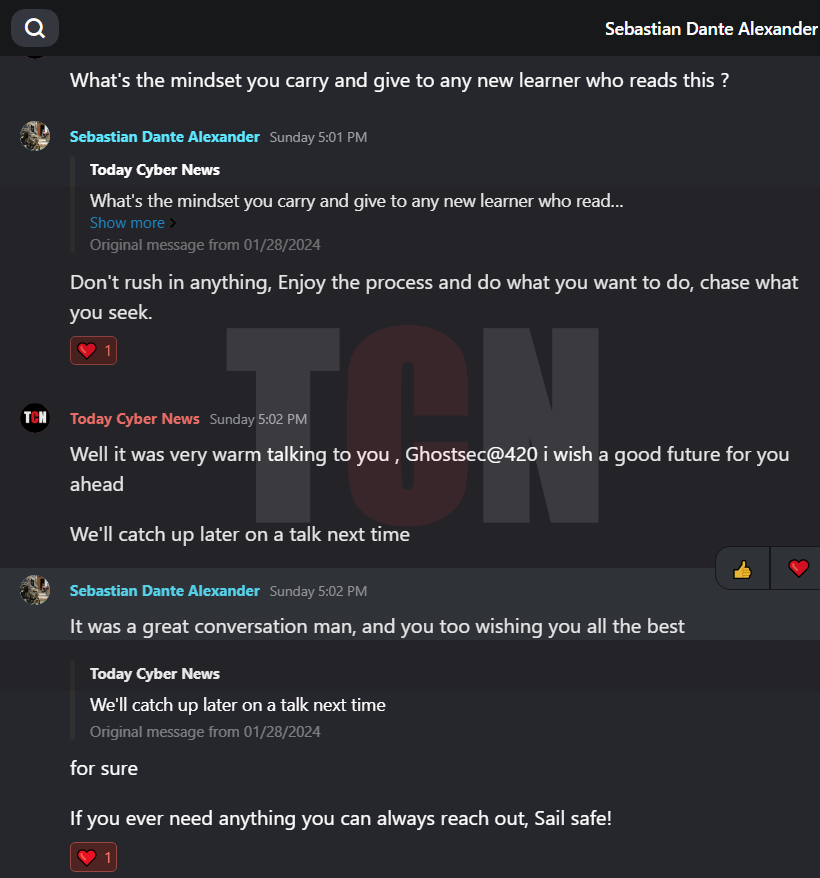
Finally, we would like to point out that there is still an unknown threat because PT Kereta has not gotten in touch with the hacker group, which has left us in a mystery. If the deadline is not met, there will be a significant data leak. In any case, we will keep our readers informed about this matter and every action that is happening right in front of your eyes will only be revealed through Today Cyber News
Frequently Asked Questions
Privacy invasions in the AI facial recognition technology ?
As far as we discussed with the hacker, he reveals that they have data but they won’t be revealing it to not trouble the regular citizens who are not part of this event.
What is the PT Kereta Api ?
PT Kereta is the Railway Operator in Indonesia, which is owned by the government of Indonesia.
How did the hackers manage to infiltrate the system ?
They did it via the social engineering worker’s account and then continued to get more data from the Kereta portal.
What is the Demand or ransom they have asked against the leak?
As per the interview the group demanded 150k to settle down the leak and move forward.
Will the hackers be leaking the AI Facial recognition data ?
We found out that their current plans do not point to leaking the data as it depends on the decision of all the other groups.